Exchange Integration
You will be charged 1 AI unit per created comment, or per updated comment (based on the email's Message ID) if its text was modified.
Overview
The Exchange intergration provides a convenient, easy-to-setup way to sync your development and production email data into Re:infer in real time.
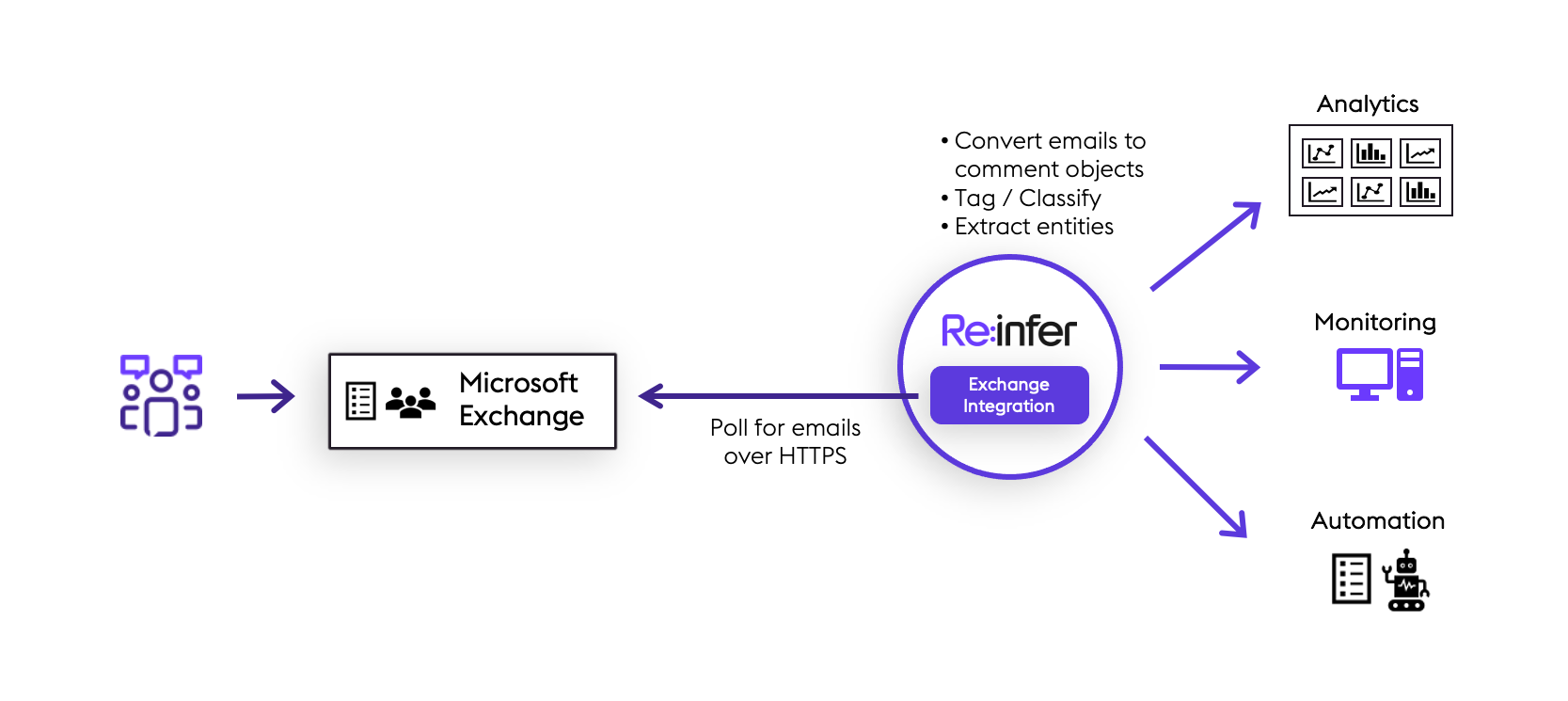
The Exchange integration continuously polls your Exchange server for new emails in the configured mailboxes. The emails are cleaned, enriched, and converted into Re:infer comment objects, and can be accessed by users on the Re:infer web platform, and by applications or bots via the Re:infer API. The Exchange integration runs in the Re:infer cloud.
The mailboxes to poll can be conveniently configured in the Re:infer UI, which also offers the functionality to start or stop the integration, and to update the configuration parameters used to connect to your Exchange server.
The Exchange intergration is compatible with Exchange Online, and with Microsoft Exchange 2010-2019 server using Exchange Web Services (EWS).
The Exchange intergration polls the Exchange server by making authenticated GET requests over HTTPS. The Exchange intergration receives data via the GET requests it initiates, and does not accept any inbound connections initiated elsewhere. The Exchange integration can be configured with specific ciphers.
It is sufficient to give the Exchange integration read-only access to your mailboxes.
How emails are synced
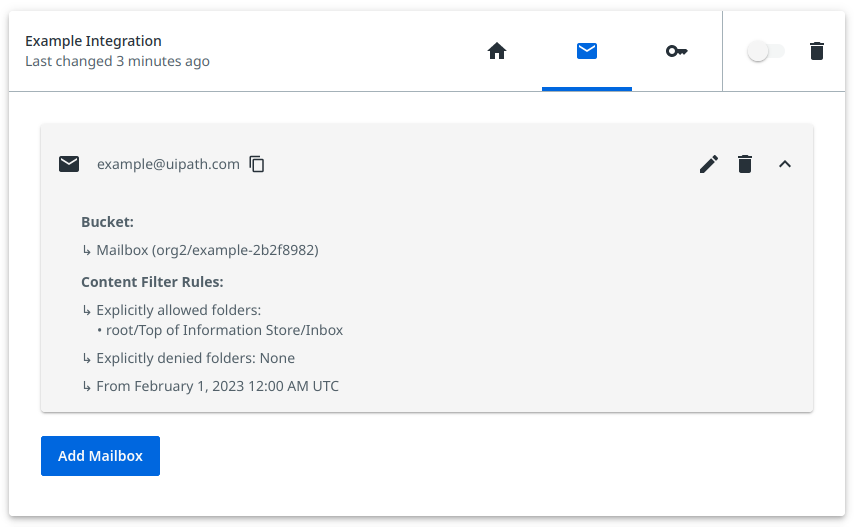
The integration will continuously sync emails from each configured mailbox. If no starting time is provided, all emails will be synced.
The integration will set the comment's comment_id to the hex-encoded
Message ID of the synced email. If multiple mailboxes containing the same
email (e.g. due to being CC'ed on the same email) are synced into the same
bucket, the resulting comment will have the metadata of the last synced of the
duplicate emails.
The integration will update the Folder user property of a comment when the corresponding email is moved to a different folder. The integration won't update the comment subject or body if either is updated in the email after it has been sent or received.
Configuration
Exchange Online
Please follow the step-by-step configuration guide.
Self-hosted Exchange Server
Please set up an NTLM service account and grant the service user read access to the mailboxes you want to sync.
Collect the following details:
- Exchange server URL
- Username and password of the service user
- Access type (Delegate or Impersonation)
- List of mailboxes to be synced
Configure the Exchange integration as described in the "Create a new integration in Re:infer" part of the tutorial, choosing the NTLM option and entering the above details.